TryHackMe Advent Of Cyber 3 (2021)
These CTF write-ups contain spoilers
Written: 2021/12/03
Day 1 - Web Exploitation - Save The Gifts
Challenge notes
Story The inventory management systems used to create the gifts have been tampered with to frustrate the elves. It’s a night shift, and McStocker comes to McSkidy panicking about the gifts all being built wrong. With no managers around to fix the issue, McSkidy needs to somehow get access and fix the system and keep everything on track to be ready for Christmas! Learning Objectives
- What is an IDOR vulnerability?
- How do I find and exploit IDOR vulnerabilities?
- Challenge Walkthrough.
Day 2 - Web Exploitation - Elf HR Problems
Challenge notes
Story McSkidy needs to check if any other employee elves have left/been affected by Grinch Industries attack, but the systems that hold the employee information have been hacked. Can you hack them back to determine if the other teams in the Best Festival Company have been affected? Learning Objectives
- Understanding the underlying technology of web servers and how the web communicates.
- Understand what cookies are and their purpose.
- Learn how to manipulate and manage cookies for malicious use.
The aim of this exercise is to use and manipulate cookies to bypass authentication. Within this challenge we are presented with a website and are asked to register an account on it. The site itself looks like this:
Using the Sign Up button, we are presented with a form that asks us to provide our Name, a Password and an Email Address. Filling this form out and submitting the form takes us to a new page that indicates to us that registration has been disabled:

However, using the Google Chrome DevTools, we can see what cookie has been set for our interaction with the site. This can be done by opening up the DevTools (pressing F12 or right click within the page and click Inspect) and navigating to the Applications tab. Within the left panel, we can find the cookies that are associated with the page.
This helps us get the first answer to the challenge’s questions:
Answer
user-authInspecting the cookie value gives us the next step in the puzzle. It took me a moment to figure out what type of encoding is used. I initially ventured down on the belief that it was Base64 but that was incorrect. I tried anumber of other encoding types to convert the string the cookie contained and eventually I found the solution.
Answer
7b636f6d70616e793a2022546865204265737420466573746976616c20436f6d70616e79222c206973726567697374657265643a2254727565222c20757365726e616d653a2254657374227dHexadecimalIn turn, decoding the string allows us to identify the answer to the next question:
Answer
{company: "The Best Festival Company", isregistered:"True", username:"Test"}jsonNow that we’ve identified the cookie, decoded it and reviewed the content, we are onto the next part of this challenge. We need to manipulate the cookie in order to bypass the login. We are given a hint that the administrator’s username is admin. In the above scenario to decode the cookie value, I was using CyberChef, which is a great tool to easily encode/decode strings. Our next step is to alter the cookie value with our payload, encode it again and replace the existing value within our browser.
Answer
{company: "The Best Festival Company", isregistered:"True", username:"admin"}7b636f6d70616e793a2022546865204265737420466573746976616c20436f6d70616e79222c206973726567697374657265643a2254727565222c20757365726e616d653a2261646d696e227dAs mentioned, adjusting the cookie with our manipulated cookie value, we can update the browser’s cookie and refresh the page. If successful, we will be taken to the Best Festival Monitoring Dashboard. This page also gives us the answers to the final questions:
Answer
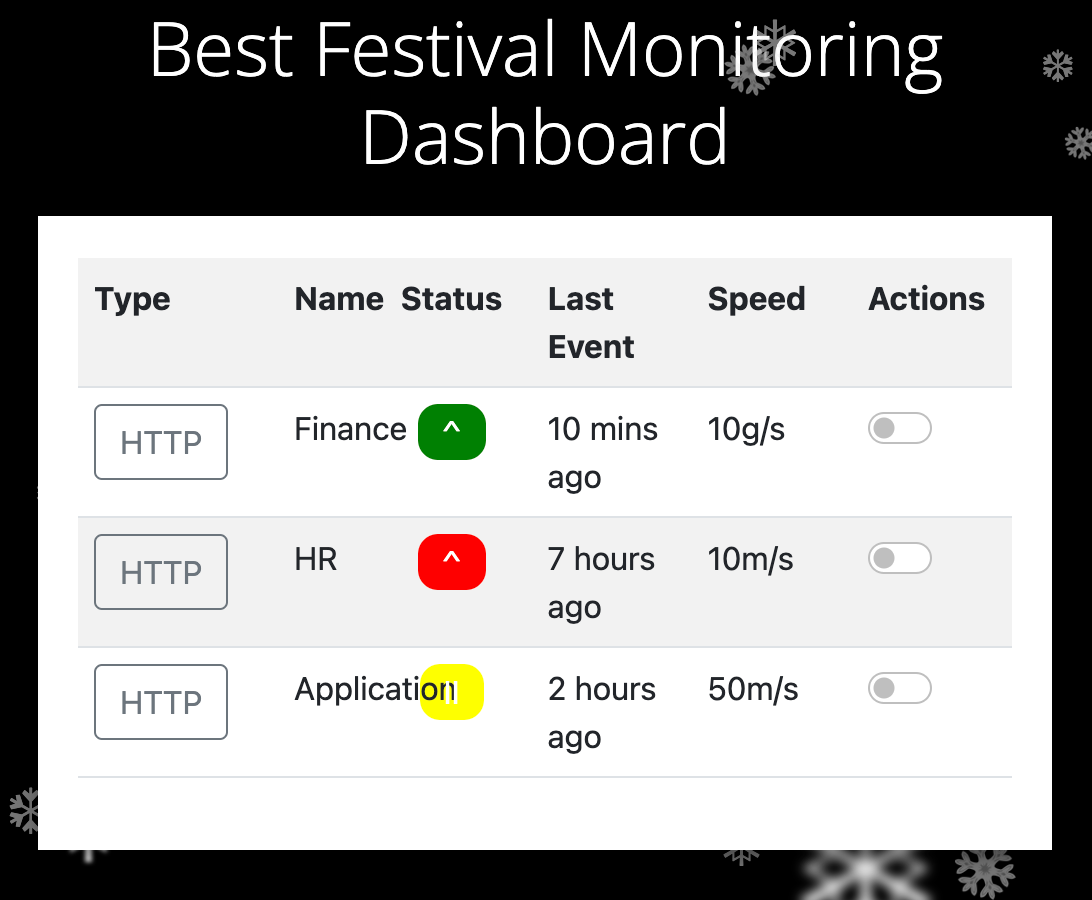 What team environment is not responding?
What team environment is not responding?
HRApplicationFor the most part, I was familiar with how cookies work overall and how web servers use them, but the overall refresher and guidance provided for this challenge. This definitely help explain some terms I’ve run into in the past, such as SameSite, HttpOnly and Secure when referencing cookies. These were primarily in the context of trying to set these policies on the server side when handling cookies, but I am sure they’ll be useful in the long run too.
A lot of external resources also did not yield a standard for encoding cookie values. Some resources that were useful in my research:
- HTTP Cookies Explained - Encoding
- Inspect the value of a cookie in JavaScript
- Encode Cookie Values
- Set-Cookie - This provides additional detail about the Set-Cookie HTTP header and its arguments, including the ones mentioned above, however covers encoding within cookie values.
Day 3 - Web Exploitation - Christmas Blackout
Challenge Notes
Story Grinch Enterprises have also tried to block communication between anyone at the company. They’ve locked everyone out of their email systems and McSysAdmin has also lost access to their admin panel. Can you find the admin panel and help restore communication for the Best Festival Company. Learning Objectives In today’s task, we’re going to be using our investigatory skills and techniques to discover un-listed content, and attempt some common authentication using the clues around us.
In this challenge we are introduced to Dirbuster, a great tool for discovering assets. In a nutshell, the tool uses wordlists to scan a target for files and paths that may exist that can be of interest to an attacker. We are also given some suggestions for wordlists that already exist on the TryHackMe machine that can be started up.
SecLists gives us a high number of pre-compiled wordlists. I poked around their GitHub repo to find what may be the most applicable in this case and came across Discoery/Web-Content/Logins.fuzz.txt. This has a number of suggested login page links that Dirbuster can search for.
I kick started my scan using the following command:
dirb http://10.10.181.131 /usr/share/wordlists/dirb/Web-Content/Logins.fuzz.txtThis pretty quickly returned a couple a few results, which also help answer our question:
Answer
adminOnce I identified the login portal’s link, I was able to interact with the login form. The information for the challenge indicates that the username is likely to be the default administrator and we are tasked with trying some default credentials. This then yielded the answer to the next question, allowing a successful login:
Answer
administratorThe last challenge question is to find the flag on the page that we logged in to:
Flag
THM{ADM1N_AC3SS}I’ve previously used fuzzing and trying to identify web-content on sites, so this was not a topic that was completely new to me. Overall the guide was helpful in laying the groundwork on how fuzzing works and some practical experience using the machines provided by TryHackMe have been great as well as wordlist resources.